
Tl; Dream
- Android 16 adds a new security feature that can warn you when your phone may be connected to a false or uncertain mobile network created by a “stingray” device.
- This feature notifies you of unencrypted connections or when the network asks for the phone’s identifiers, which can help detect when monitoring can occur.
- Due to new hardware requirements, this protection will probably only be on new devices that are launched with Android 16, such as the upcoming Pixel 10.
There are many simple things you can do to keep your private information safe, such as using strong passwords, examining apps and just installing apps from reliable sources. However, some attacks are much more difficult to protect you from, as they are so sophisticated and stealthy that they can happen without ever noticing it. Such an attack lurks your phone into connecting to a false, uncertain mobile network, which is difficult for the average person to detect. Fortunately the new Android 16 Update has a feature that may be able to warn you when someone uses this tactic to sniff on you.
This type of attack uses a device called a “stingray.” An attacker sets up this device near a target they want to monitor, and it mimics a legitimate cell tower. The stingray lurts near mobile devices to connect to it so that the attacker can collect unique identifiers (such as IMEI) and even force them into an older, more uncertain communication protocol. These identifiers allow attackers to target specific units for analysis, while switching protocols can let them cut off unencrypted text messages and telephone calls.
These “stingray” devices are used notoriously by law management agencies, but their technology can also be acquired by malicious actors. While some argue that they are a necessary tool for monitoring criminals, the potential for abuse is significantly, as they can be used to collect hidden data on ordinary people. Because of this, Google has been working on ways to warn Android users or prevent them from sending communication over unsafe cellular networks.
With the release of Android 12For example, Google added support to disable 2G connection at the modem level. IN Android 14The company followed up by supporting deactivation of connections that use zero -chiffer – a form of unencrypted communication. More recently, Android 15 Added support to notify the OS when the network asks for the device’s unique identifiers or tries to force a new chifferal. These functions directly counteract the tactics used by commercial “stingrays”, which are lurking units to downgrade to 2G or use zero cheems to make traffic easier to cut off. Blocking these connections and notifying the user about these requests helps them against monitoring.
Mishaal Rahman / Android Authority
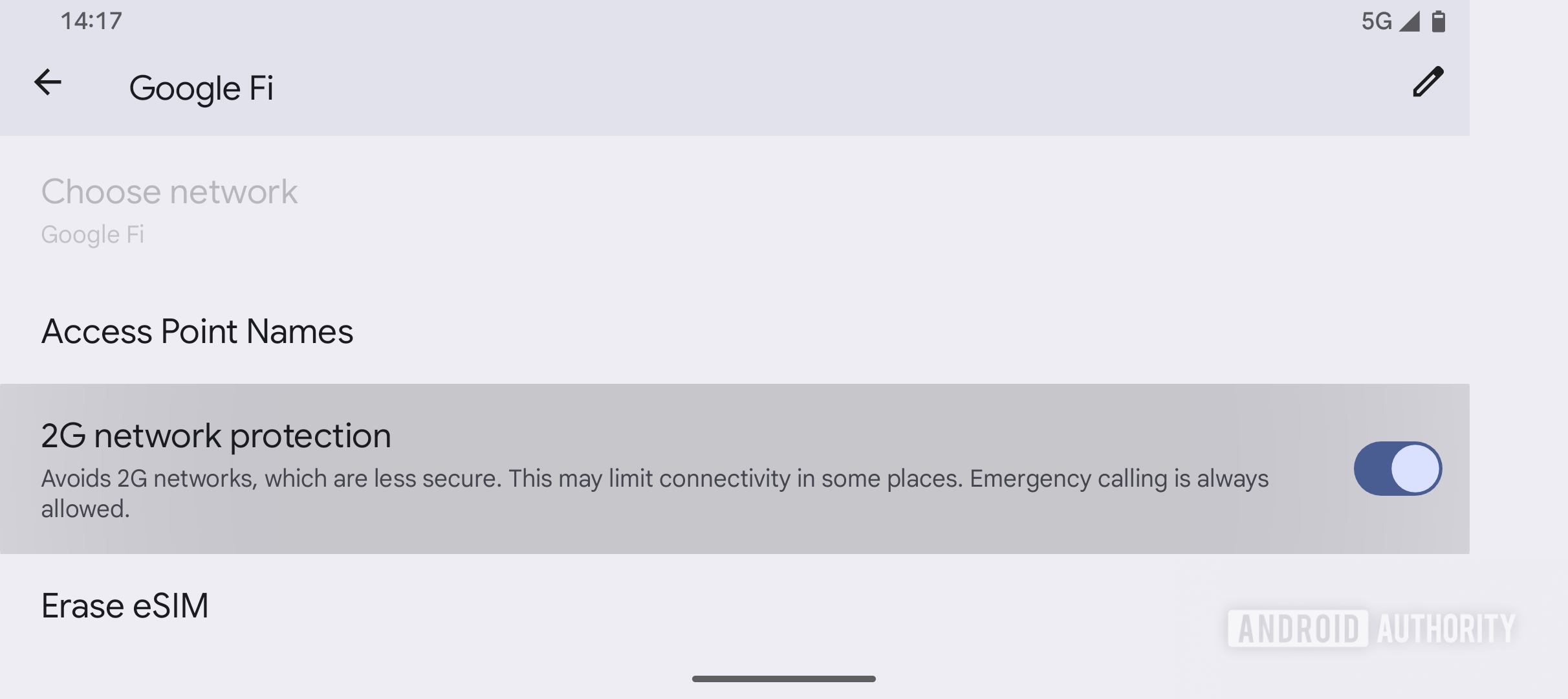
The change to disable 2G networks in Android 16 on a Pixel 9a.
Unfortunately, just one of these three features is widely available: the ability to disable 2G connection. The problem is that the implementation of these protections requires similar changes in the phone’s modem driver. The function that notifies the operating system of identifier requests, for example, requires a modem that supports version 3.0 of Android’s Iradio Hardware Sabstraction Team (Hal). This addiction is the reason for these Security features are missing on current pixel phones And other devices, and it is also likely why Google delayed launch of the dedicated “Mobile Network Security” settings page it planned for Android 15.
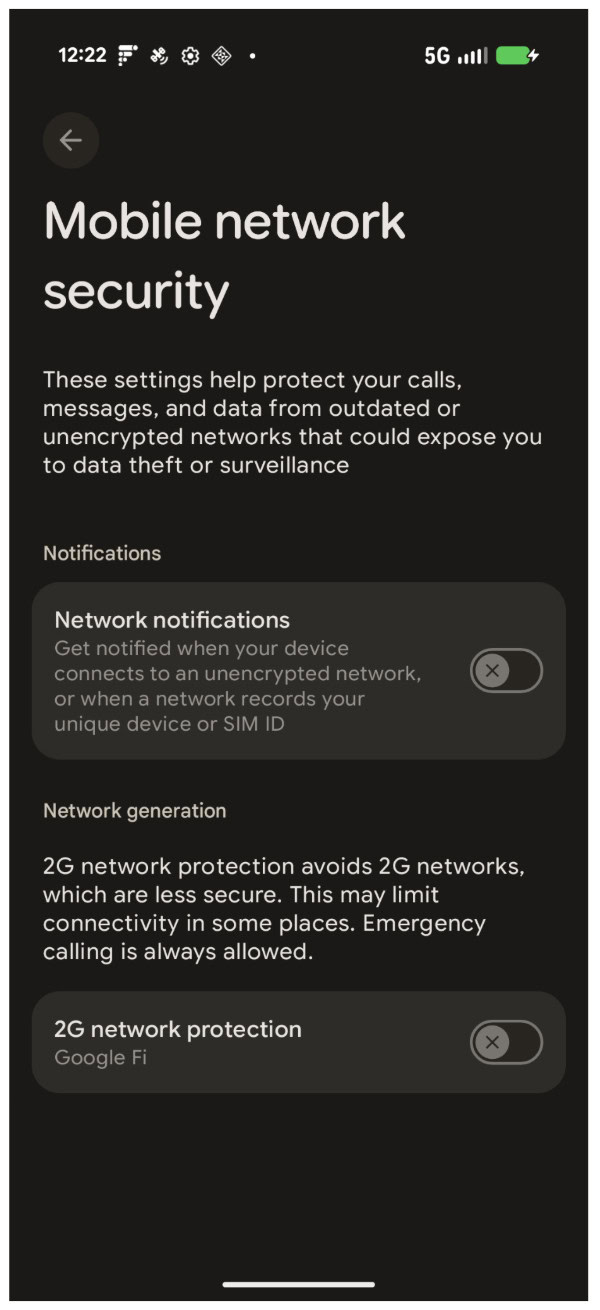
Since upcoming devices launched with Android 16 will support version 3.0 of Androids Iradio Hal, Google is reintrord “Mobile network security“Setting page in the Security Center (Settings> Security and Privacy). This page contains two sub -sections:
- Alert
- This sub -section contains a “Networking“Exchange. When enabled, it allows the system to warn you if the device connects to an unencrypted network or when the network asks for the phone’s unique identifiers. This change is disabled by default in Android 16.
- Network generation
- This sub -section has a “2g network protection“Exchange that enables or disables the device’s 2G connection. This is the same exchange found in the Main SIM setting menu, and it is also disabled as standard in Android 16.
Since “Mobile Network Security” will only appear on devices that support both “2G Network Protection” connectivity and the “Network Alerts” feature. This is why it does not appear on the current Pixel devices running Android 16, as they lack the necessary modem support for the network alert function.
When the “Network Alerts” feature is enabled, Android will post a message in the alert panel and security center when your device switches from an encrypted to an unencrypted network, or vice versa. It will also enter a notice in both places when the network gets access to the phone’s unique identifiers, and describes the time and the number of times they were asked.
It is worth noting that legitimate cellular networks need to access the device’s unique identifiers from time to time, such as when your device connects to them after leaving flight mode, so network notifications do not turn out to be malinent. Android has no way of actually knowing if a cell tower is real or not, so it is quite easy to give the user to the user and let them decide whether to take action.
Now that Google has launched this security page in Android 16, it will not be long before we start looking at devices. However, because of Google requirements freeze (GRF) The program policy that allows OEMs to lock hardware-related devices when launched-it is unlikely that current devices will be updated to support the notification feature. We will most likely have to wait for upcoming devices launched with Android 16, for example Pixel 10 series, to see this protection fully implemented.
This article was updated at 18:04 to make it clear that Android’s “network notifications” do not act as true indicators that the device is actually connected to a false cell tower, but rather as warnings for the user warnings that this can happen.


